For the scope of this article, we’ll take a look at services in Microsoft Azure that support you in securing your overall cloud infrastructure that builds the foundation for your cloud-native application. It is top of the mind for all cloud vendors to provide professional tools to harden and secure cloud infrastructures. Microsoft has recently re-branded existing services to group and advertise all essential services for securing cloud services under the brands Microsoft Defender for Cloud and Microsoft Sentinel.
Article Series
- Part 1: Code, Container, Cluster, Cloud: The 4C’s of Cloud-Native Security
- Part 2: Container Security: The 4C’s of Cloud-Native Security
- Part 3: Cluster Security: The 4C’s of Cloud-Native Security
- Part 4: Code Security: The 4C’s of Cloud-Native Security
- Part 5: Cloud Security: The 4C’s of Cloud-Native Security ⬅
Before we quickly dive into Microsoft Defender for Cloud, we will look at both products offered by Microsoft and which needs they address.
Microsoft Defender for Cloud
Microsoft Defender for Cloud addresses three essential needs when it comes to securing cloud services:
- Continuous Assessment: By providing a single number – the secure score -, Microsoft Defender for cloud helps you understand your security posture. A higher secure score means a more secure cloud environment.
- Secure: Microsoft Defender for Cloud also assists in actively securing cloud infrastructures. It provides security recommendations that tell you which services have weak configurations and may increase your overall attack surface. On top of delivering those recommendations, Microsoft Defender for Cloud gives you either fine granular instructions on how to remediate those misconfigurations or lets you fix those findings automatically by just clicking a “Fix” button.
- Defend: Quickly taking action on potential threats or attacks is mission-critical to defense cloud environments. Microsoft Defender for Cloud detects attacks and threats to your resources and alerts you automatically. You can stream those alerts also to different SIEM and SOAR solutions.
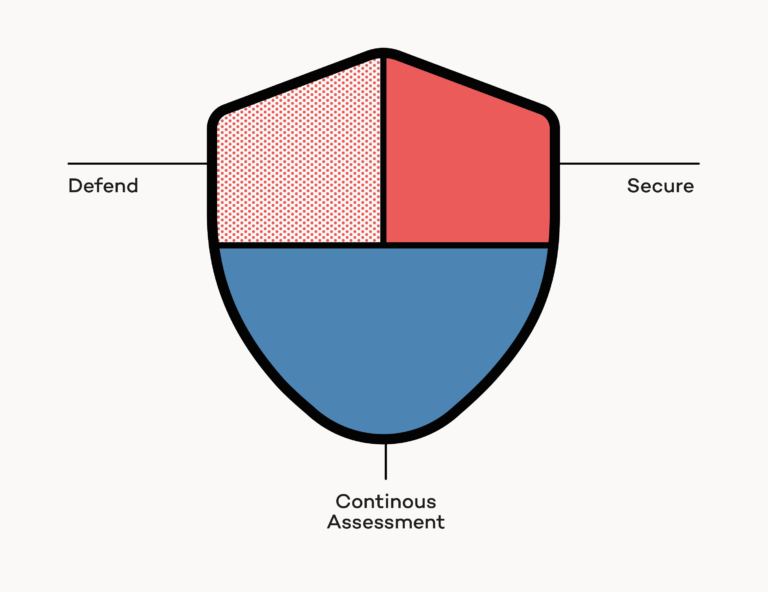
The Continuous Assessment and Secure capabilities Microsoft Defender for Cloud address Cloud security posture management (CSPM) . Microsoft Threat intelligence powered alerts (Defend) capabilities are key features that address Cloud workload protection (CWP).
Microsoft Sentinel
Besides Microsoft Defender for Cloud, Azure customers can use Microsoft Sentinel, a security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution. Microsoft Sentinel allows you to:
- Collect data across all cloud services, applications, users, and infrastructure
- Detectanomalies and eliminate false positives using threat intelligence
- Investigate threats with AI to hunt and stop suspicious activities
- Respond rapidly using built-in orchestration and automation of recurring tasks
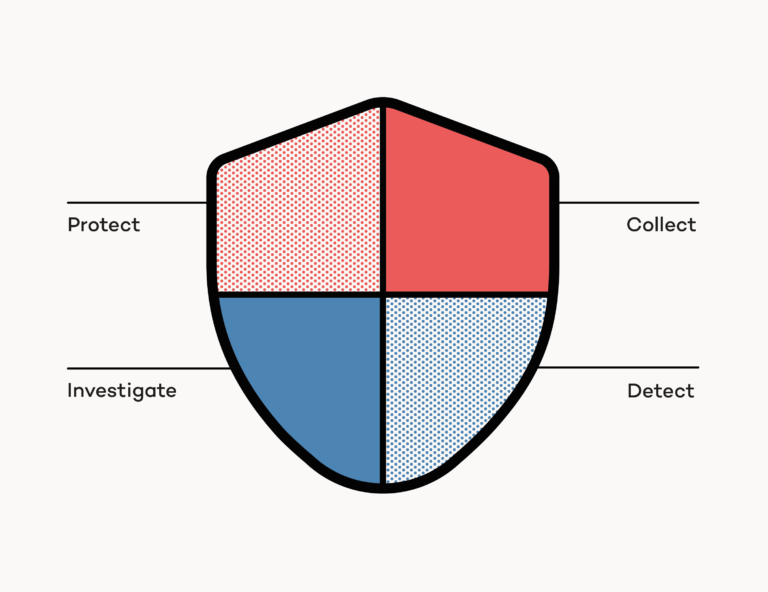
With Microsoft Sentinel, users can collect and integrate data from different sources using built-in connectors. You can incorporate data from services like Microsoft 365, Azure AD, and several Microsoft Defender products like Microsoft Defender for Identity or Microsoft Defender for Cloud Apps. On top of that, you can integrate data from non-Microsoft environments using well-adopted formats like Syslog or ingest custom data via REST. Once data ingestion is configured, you can use workbooks (powered by Azure Monitor Workbooks) to visualize and monitor your data. Although Microsoft Sentinel comes with pre-configured workbooks, you can create tailored workbooks on your own to address individual needs. Visualizing and monitoring a vast amount of data becomes cumbersome and tedious quickly. Analytics capabilities from Azure Sentinel reduce noise and minimize the number of alerts you’ve to care about. Microsoft Sentinel correlates alerts into incidents. You can customize the built-in correlation rules to fit your needs. On top of fundamental correlation rules, Sentinel uses its machine learning (ML) capabilities to create incidents from network behavior anomalies. At this point, you should already realize that data ingestion and visualization are just the tip of the iceberg. Although Sentinel is a supercritical piece of the puzzle, I’ll stop here and won’t touch other features from Microsoft Sentinel like automation, integration, hunting, and incidence response techniques. You should definitely consult the official Microsoft Sentinel documentation and dive deeper. But for the scope of this article, let’s move again back to CSPM.
Getting started with CSPM
Now that you have some fundamental understanding of Microsoft Defender for Cloud let’s get started with CSPM.
Choose your Microsoft Defender for Cloud tiers
Microsoft Defender for Cloud offers a free tier that includes continuous assessment and security recommendations. It will give you a secure score (we will take a look at this in a bit) for Azure and AWS environments. (Yes, you can assess multi- and hybrid-cloud environments with Microsoft Defender for Cloud). Enhanced security features provided by Microsoft Defender for Cloud can be activated on the Azure subscription scope. However, there is a 30-day trial that you can use to try those advanced capabilities.
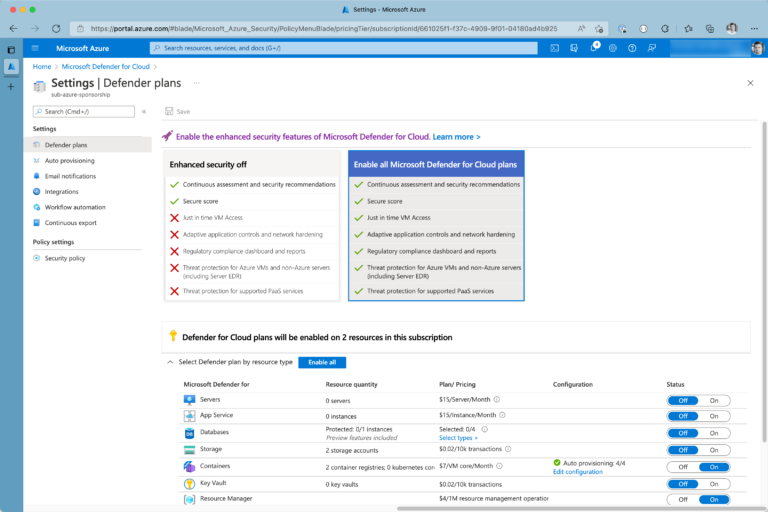
Enhanced security features can be activated/deactivated by resource type. For example, if you’re working with containers, you may find Microsoft Defender for Containers very useful. However, in contrast, you may not need to rent Microsoft Defender for PostgreSQL if your PostgreSQL deployments in Azure are just for testing or development purposes. You can access your Defender for Could dashboard by navigating to Microsoft Defender for Cloud from Azure Portal. The dashboard provides not just essential insights about your overall cloud security; it also contains the latest recommendations from Microsoft security experts in one place.
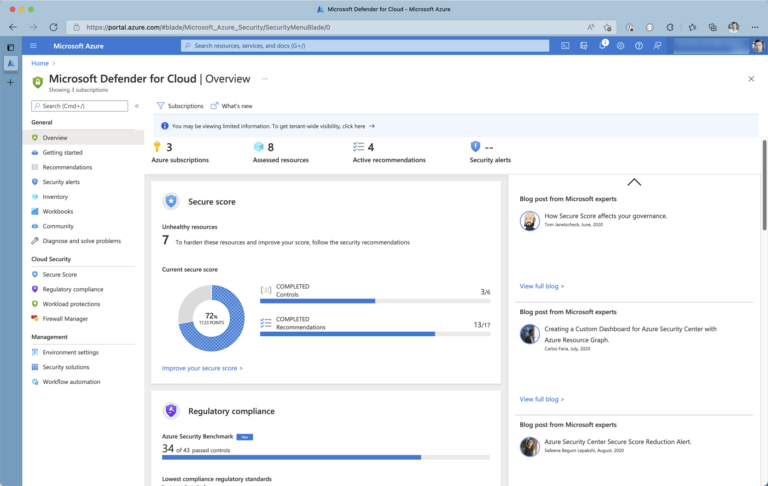
To configure tiers and book enhanced security features, you can navigate from the dashboard to Environment settings using the left-hand blade navigation.
Configure E-Mail notifications
Security-related notifications and alerts must be sent to people that can take action on discovered incidents. You should take a second and configure your E-Mail notifications properly. To avoid flooding inboxes with notifications and to reduce noise, Defender for cloud will limit the volume of outgoing mails for each subscription to:
- max 1 mail per 6 hours for alerts with high severity
- max 1 mail per 12 hours for alerts with medium severity
- max 1 mail per 24 hours for alerts with low severity
Again, you can customize those settings on the subscription scope.
Configure regulatory compliance
Do you have to address specific regulatory compliance? With Microsoft Defender for Cloud, you can continuously compare the actual configuration of your cloud resources against requirements defined as part of industry standards and benchmarks.
Continuously checking for a regulatory standard requires enhanced security being enabled. You can choose a regulatory standard – again on subscription level – by enabling it under Security policy.
Once you’ve configured your Security policies, it will take several hours to see your performance in the context of every selected regulatory standard in the compliance dashboard. Check the list of supported regulatory standards, to see where Microsoft Defender for Cloud can help hit the bar.
Secure score
Microsoft Defender for cloud computes a secure score, a percentage value that reflects your overall security situation at the current point in time. The security situation changes continuously because of new vulnerabilities, new attack surfaces being added to the cloud infrastructure, or new security features being added to the platform itself. You can see from the picture below that you get a secure score calculated per subscription on top of the overall secure score.
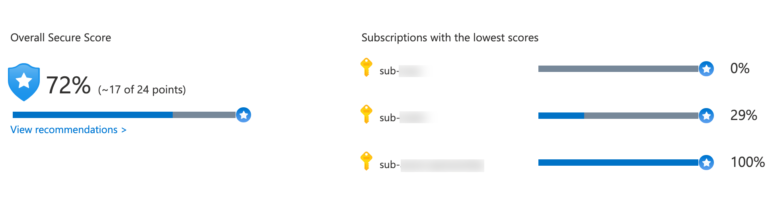
Subscription-based secure scores are an immediate indicator of how you can improve your overall cloud security. Also, keep in mind that the secure score is not just a number made up by some teams at Microsoft. It’s reproducible, and the underlying formula is publicly available and well documented.
Recap
This article looked at fundamental concepts for securing your cloud platform. Services like Microsoft Defender for Cloud assist you in discovering insecure service configurations and ensure continuous service observation according to the latest security standards.
When hosting applications in the public cloud, we must address security concerns and harden underlying cloud services to prevent attackers from executing various attacks such as taking down the application, stealing data, or acting on behalf of a user.
Securing the cloud addresses the last “C” in the 4C’s of cloud-native security, which marks the end of the article series.